Why consider Secure Access Service Edge?
The early era of cybersecurity relied on firewalls, on-premises web proxies, sandboxing, SIEMs, and endpoint security, all of which aren’t equipped for a cloud-dominated space. These days more and more data is moving outside the network perimeter, beyond the reach of firewalls which aren’t equipped to read cloud traffic anyway. Couple this with the growing number of endpoints connecting to enterprise networks are BYOD. In total, you have a recipe for extremely unreliable oversight of company data.
Because of all these needs, your traditional perimeter has disappeared, and you must move your inspection point.
Modern Solutionz Security Services are all about getting leverage back.
By utilizing proven SASE solutions, we can architect multiple distributed inspection points that get as close as possible to where and how data is accessed, whether it’s in the cloud or a private application.
Secure Access Secure Edge (SASE)
SASE is a comprehensive security framework that redefines how organizations approach network security. It moves away from traditional network-centric security models towards a more holistic and dynamic approach that considers both the identity of users and the context in which they are accessing resources.
This has profound implications for how you design security and infrastructure, and why we now need SSE and SASE to help us get organized. Think of it this way: if 90 percent of your security spend is for on-premises-focused security, but 50 percent of your apps and 90 percent of your users are off-premises, your security is already being stretched like a rubber band. You’re trying to pull security from the on-premises model into all of these other things it wasn’t designed for, creating tension for the business and leading to an eventual snap of that rubber band, breaking your security. That won’t work.
SASE architecture
Secure Access Service Edge, or SASE, unifies networking and security services in a cloud-delivered architecture to protect users, applications, and data everywhere. Given that users and applications are no longer on a corporate network, security measures can’t depend on conventional hardware appliances at the network edge.
Instead, SASE solutions promise to deliver the necessary networking and security as cloud-delivered services. Done properly, a SASE model eliminates perimeter-based appliances and legacy solutions. Instead of delivering the traffic to an appliance for security, users connect to the SASE cloud service to safely use applications and data with the consistent enforcement of security policy.
What are the Major transformations behind SASE Architecture?
The key objectives or grand strategy of security, of protecting data and data access have remained the same. The problem is that the applications that the data is hosting in and the workforce accessing the data is now highly distributed. So, it doesn’t make sense to have multiple policy enforcement points across these various distributed communication streams and then expect them to deliver consistent controls or even communicate with one another.
Instead, we need a centralized policy enforcement point, preferably sitting in the cloud that understands the data context and the language of the cloud and all that traffic is then steered through it. And that is SASE.
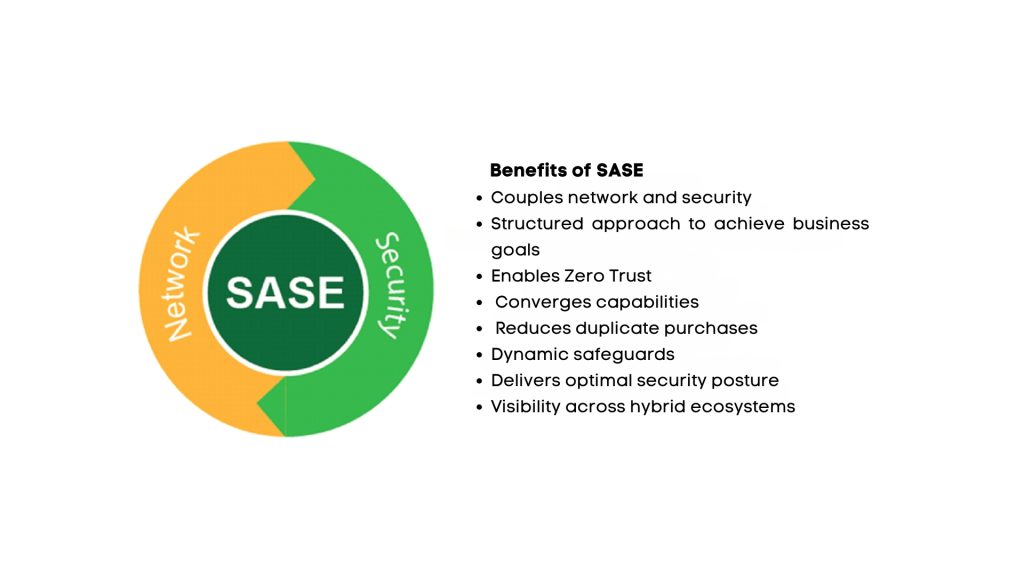
SASE benefits:
A SASE network architecture offers enhanced security, improved performance, simplified management, scalability, cost efficiency, compliance alignment, and futureproofing. By adopting SASE, organizations can establish a flexible, secure, and agile network infrastructure that addresses the demands of the modern digital landscape.
Flexibility: Allows for direct-to-net or direct-to-cloud access from anywhere for easy adoption of new digital business models
Cost savings: Eliminates CapEx for on-premises infrastructure and provides lower, predictable OpEx due to its Security-as-a-Service model.
Reduced complexity: Consolidated services into a cloud-delivered model eliminates complex stack of legacy point solutions and simplifies operational effort.
Increased performance: Enhances and accelerates access to internet resources via a global network infrastructure optimized for low-latency, high-capacity, and high-availability.
Zero trust network access: Provides secure, contextual access to private apps in public/private clouds.
Threat protection: Stops cloud and web attacks such as cloud phishing, malware, ransomware, and malicious insiders.
Data protection: Protects data everywhere it goes, inside and outside of the organization, including within public clouds as well as between company and person instances of cloud apps
What’s the difference between SASE and SSE?
SASE – Networking and security services in one package
SSE – Security Service Edge – It is the security side of SASE.
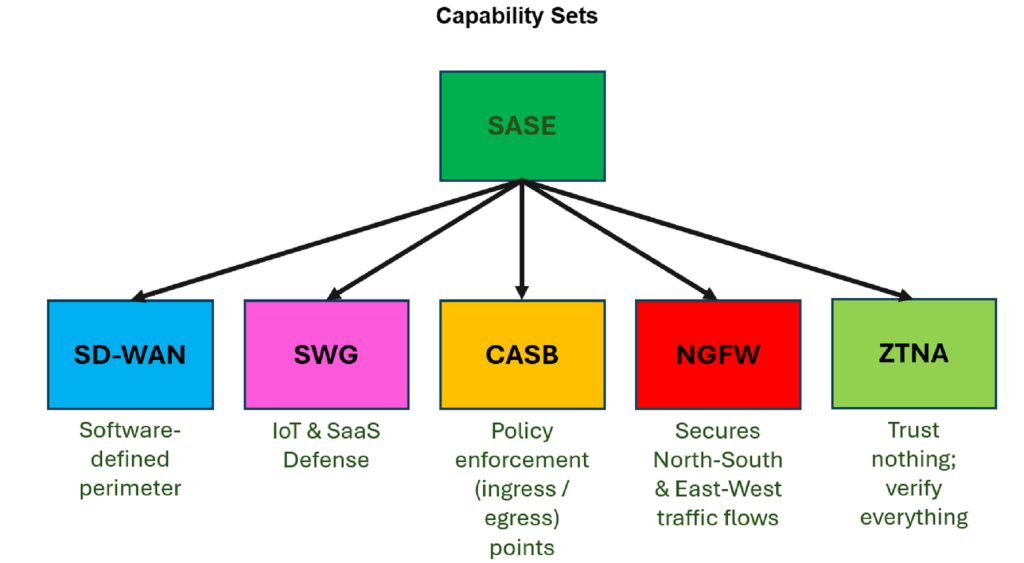
SSE = (SWG + CASB) + ZTNA
(Web + API) = (Network + OS)
Secure Service Edge (SSE) Technologies encompasses
Secure Web Gateway (SWG): By ensuring secure access to the web and protecting against web-based threats, SWG solutions play a crucial role in SSE. They provide essential features like URL filtering, malware protection, and data loss prevention to safeguard users as they access online resources.
Cloud Access Security Broker (CASB): CASBs extend security controls to cloud services and applications, addressing the unique challenges associated with cloud environments. As part of SSE, CASB solutions provide visibility into cloud usage, enforce security policies, and protect data through encryption, access controls, and threat detection mechanisms.
Zero trust network access (ZTNA)/VPN: ZTNA is a fundamental component of SSE, enabling secure access to applications regardless of user or device location. ZTNA solutions ensure that access decisions are based on identity verification and contextual factors rather than relying solely on network perimeters, aligning with the principles of zero trust security.
Let’s delve a bit deeper into how ZTNA works and its significance in modern cybersecurity:
Principle of Zero Trust: Zero Trust is based on the notion of “never trust, always verify.” This means that access to resources is never granted implicitly based on factors like network location or user credentials alone. Instead, access is continuously verified based on the identity of the user, the security posture of the device, and other contextual factors.
Continuous Verification: ZTNA solutions ensure that access decisions are based on continuous authentication and authorization processes. Users and devices must undergo ongoing verification to access resources, and access is only granted if all necessary conditions are met. This dynamic approach to access control reduces the risk of unauthorized access and data breaches.
Identity-Centric Access: ZTNA focuses on identity verification as the primary means of access control. Users and devices are authenticated based on their identity attributes, such as user credentials, device posture, and behavioral patterns. This ensures that only authorized users and devices are granted access to resources, regardless of their location or network perimeter.
Contextual Factors: In addition to identity verification, ZTNA considers contextual factors when making access decisions. These factors may include the user’s role within the organization, the sensitivity of the resource being accessed, the time of access, and the location of the user or device. By taking these contextual factors into account, ZTNA enhances security and reduces the risk of unauthorized access.
Explicit Access Control: With ZTNA, access is only granted to identities and resources that are explicitly defined and verified. This means that users and devices must be explicitly authorized to access specific resources, and access is denied by default. This approach minimizes the attack surface and ensures that only trusted entities can access sensitive resources.
Overall, Zero Trust Network Access (ZTNA) plays a crucial role in modern cybersecurity by providing a dynamic, identity-centric approach to access control. By continuously verifying the identity of users and devices and considering contextual factors when making access decisions, ZTNA enhances security, reduces the risk of unauthorized access, and aligns with the principles of zero trust security.
Modern Solutionz Cybersecurity commitment to our clients
Modern Solutionz is committed to delivering comprehensive cybersecurity solutions and strategic IT direction to support your clients’ business objectives. Here’s how our approach aligns with best practices and industry standards:
Data Privacy Assurance: By prioritizing data privacy, you’re demonstrating your commitment to safeguarding sensitive information entrusted to your care. A robust Identity Access Management (IAM) strategy ensures that only authorized individuals have access to data, reducing the risk of data breaches and unauthorized access.
Strategic IT Direction: Providing strategic IT direction aligns our services with your business goals, helping to leverage technology effectively to drive growth and innovation. By understanding your lines of business, we tailor your solutions to address their specific needs and challenges, ultimately contributing to their success.
Identity Access Management (IAM): IAM plays a critical role in securing access to data and applications within your clients’ environments. By implementing IAM best practices, such as role-based access control, multi-factor authentication, and privileged access management, we can enforce strong security controls and protect against insider threats and unauthorized access.
Integration of Services: Effective integration of services ensures seamless communication and collaboration between different components of your IT infrastructure. By linking application functionality and data securely, we deliver reliable services our customers, enhancing their competitiveness and reputation in the market.
Overall, by focusing on data privacy, providing strategic IT direction, implementing robust IAM practices, and integrating services effectively, Modern Solutionz is well-positioned to meet the evolving cybersecurity and technology needs of our clients. Our proactive approach to cybersecurity and commitment to delivering value-added services will undoubtedly contribute to the success and satisfaction of our Enterprise and Public Sector clients.
« Security Validation as a Service

